Part 3: Database Management
by Dan Rachlis
 Data Mining, Data Analysis, Data Warehouse, Data Mart, Data Modeling, Data Requirements, Data Integration, Data Visualization, Data Cleansing, Data Transformation, Relational Database, Business Intelligence, Data Management, Data Architecture, Data Privacy, Data Security, Data Access, Data Integrity, Metadata, Data Backup, Disaster Recovery, Business Continuity Planning, Data Governance, Data Asset Customer Relationship Management (CRM) Software, Records Management, Data Structure, Data Movement
Data Mining, Data Analysis, Data Warehouse, Data Mart, Data Modeling, Data Requirements, Data Integration, Data Visualization, Data Cleansing, Data Transformation, Relational Database, Business Intelligence, Data Management, Data Architecture, Data Privacy, Data Security, Data Access, Data Integrity, Metadata, Data Backup, Disaster Recovery, Business Continuity Planning, Data Governance, Data Asset Customer Relationship Management (CRM) Software, Records Management, Data Structure, Data Movement
Have you ever used any of the above terms? Chances are that you have and that you may be using them incorrectly. In an era where technology is continually advancing, electronic data can be found everywhere. In the health care actuarial industry especially, data and understanding how to manage the constant flow of information is vital to an organization’s operational and financial viability. Actuaries need to be sure the analysis and opinions they provide are accurate, asking for the wrong data or not understanding what data to ask for can have a significant impact.
This article is the third in a four-part series about eliminating the confusion with using data terminology.
In part one, we discussed data governance, the formal management of data assets with respect to availability, usability, integrity, and security throughout the enterprise. Data governance ensures that data can be trusted and that people can be made accountable for any adverse event that happens because of low data quality. It assigns responsibilities to fix and prevent issues with data so that an enterprise can become more efficient.
In part two, we introduced data architecture, data analysis and design. Data architecture describes the data structures used by a business and/or its applications. The main goal of data analysis is to highlight information to draw conclusions and support decision making.
Part three will discuss data management.
A relational database is a collection of data in tabular form with common characteristics that can be linked together. A Relational Database Management System (RDBMS) is a set of computer programs that controls the creation, maintenance and the use of a database. It is the system software that controls the use of an integrated collection of data. Such a grouping of data typically uses the relational model (a technical term for this is schema).
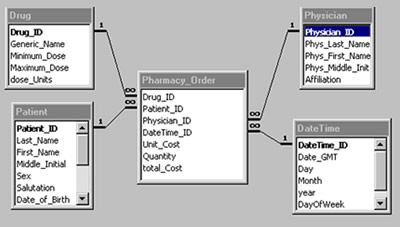
A schema is the data visualization of the database including relationships between tables. Relational databases are currently the predominant choice in storing financial records, manufacturing and logistical information and personnel data. It allows organizations to place control of database development in the hands of database administrators and other specialists. A database administrator (DBA) is a technical IT person responsible for an organization's database. The database administrator has many roles and responsibilities including:
- Overseeing the installation and ongoing function of software on a system designed for use by a number of users.
- Installation, configuration and upgrading of Microsoft SQL Server/MySQL/Oracle server software and related products.
- Establish and maintain sound backup and recovery policies and procedures.
- Implement and maintain database security (create and maintain users and roles, assign privileges).
- Database tuning and performance monitoring (indexing tables and optimizing queries).
- Application design, tuning and performance monitoring.
- Set up and maintain documentation and standards.
- Plan growth and changes (capacity planning).
Data privacy is the relationship between technology and the legal right to collect data (remember your HIPAA guidelines). The challenge in data privacy is to share data while protecting the personally identifiable information (PII). Data security is the protection of data against deliberate or accidental access of unauthorized persons. It ensures that data is kept safe from corruption and that access to it is suitably controlled. Thus, data security helps to ensure privacy. Data access typically refers to software and activities related to storing, retrieving or acting on data housed in a database or other repository. Data Access is simply the authorization you have to access different data files.
The final article in this series will focus on business intelligence and records management.
Dan Rachlis is a specialist master in the Chicago office of Deloitte Consulting LLP. He has more than 20 years’ experience in business, consulting, and data management. He earned undergraduate degrees in Mathematics and Business Administration from Southern Illinois University and a master’s degree from Loyola University in MSISM – Masters of Information Systems Management, a Certificate in Data Warehousing and Business Intelligence from Loyola University, and is an (ASA) Associate of the Society of Actuaries. He can be reached at drachlis@deloitte.com or at 312.486.5631.